As described in the last post, before we can start writing our app in PicoLisp, we need to use a little tool to interface the Java API. This is provided by the AndroidApp PilBox. At the moment of writing this post, the latest version is 22.2.23.
Installation
Like any PlayStore App, it can be installed by simply clicking on the "install" button. Opening the App shows the "Home" view of the app, which should at that point be empty.
On the upper right, there is a "Settings" icon. Clicking on it shows a page with three tabs: The first one shows a table with the installed PicoLisp apps and should be empty after installation. The second one is titled "CSS", the third one is for language settings.
On the upper left, you can find the PicoLisp Logo. Touching it toggles between the REPL and the Home screen.
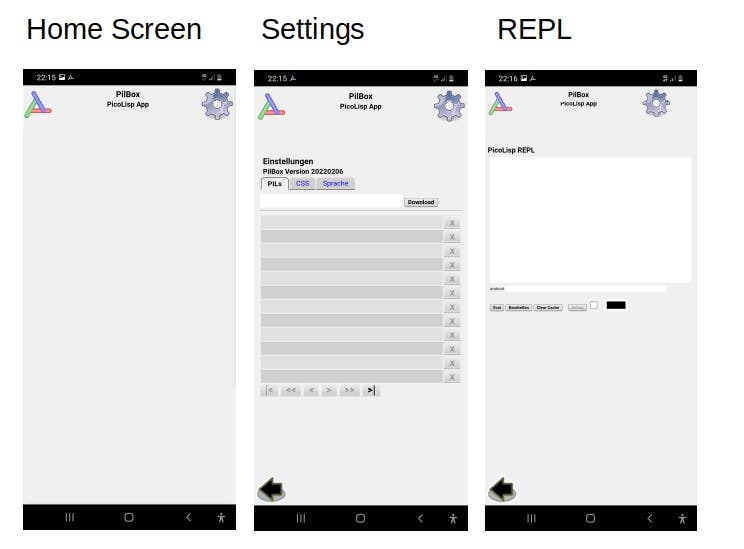
As long as the App is running, the PilBox logo is displayed among the notifications. Like most Android apps, it is closed by swiping it out from the running applications view.
Analyzing the PilBox source code
Before we get deeper into how to use the app, let's quickly check out the source code. As you might guess from the description in the last post, the PilBox is quite a powerful tool, so let's make sure that we have at least a rough understanding of what the app is actually doing.
To inspect the app's source code, you can get it as APK or TGZ from here. There are several ways to analyze android app APKs. I have opened it in the "Mobile Security Framework" Tool MobSF, which allows you to do a static and dynamic analysis of the app in a quite organized way. You can install MobSF locally or access the hosted version: mobsf.live.
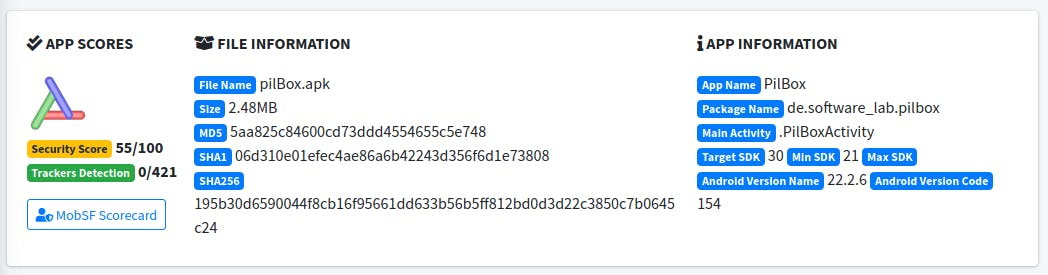
Let's open pilBox.apk in MobSF and run the static analysis. First we see some general file and aggregated "score" information. The overall security store of 55/100 is not surprising, given that the app is very powerful (although of course it does not do anything malicious, unless you load that code by yourself).
We will see later where this rating comes from in detail.
- Permissions
Next, let's take a look at the permissions. As you might have noticed, PilBox does not require any permissions during installation.
However, depending on the app which is loaded into the box, the user could be asked for the following permissions:
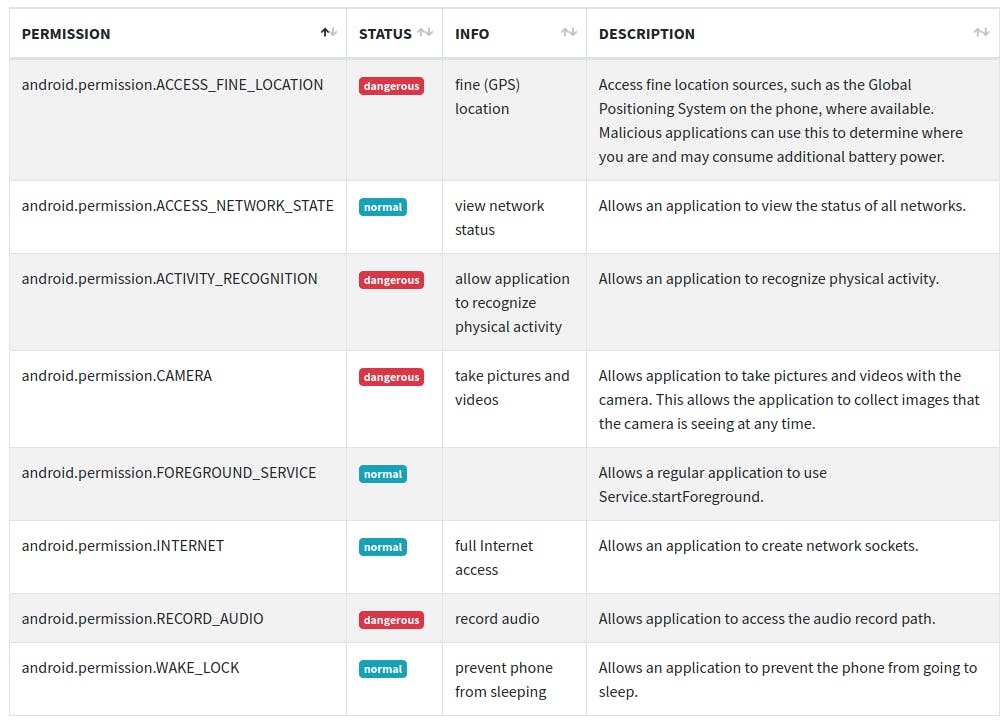
GPS and activity tracking as well as microphone and camera access are rated as "dangerous" which means that explicit consent from user side is required. The "normal" permissions are granted by default.
- Android API
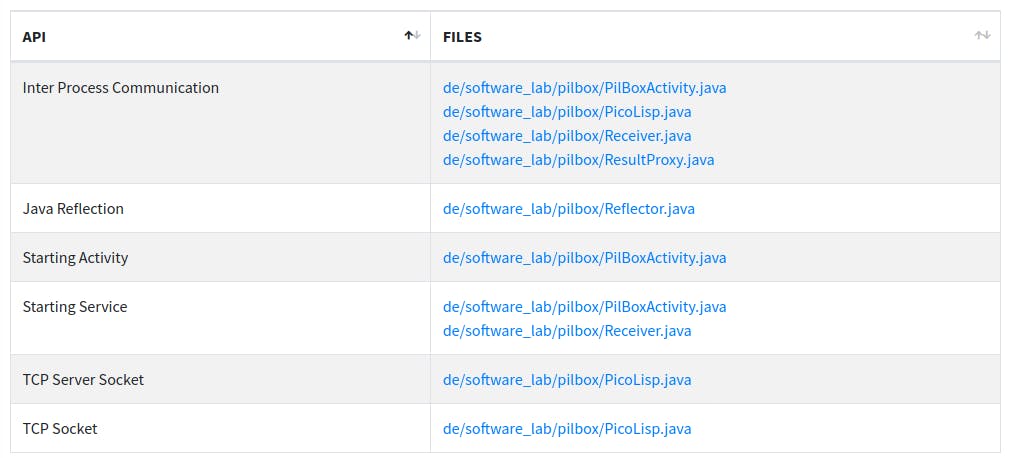
Next, we find an overview of the files which contain the app's soure code. By clicking on it, we could read the de-compiled code in cleartext.
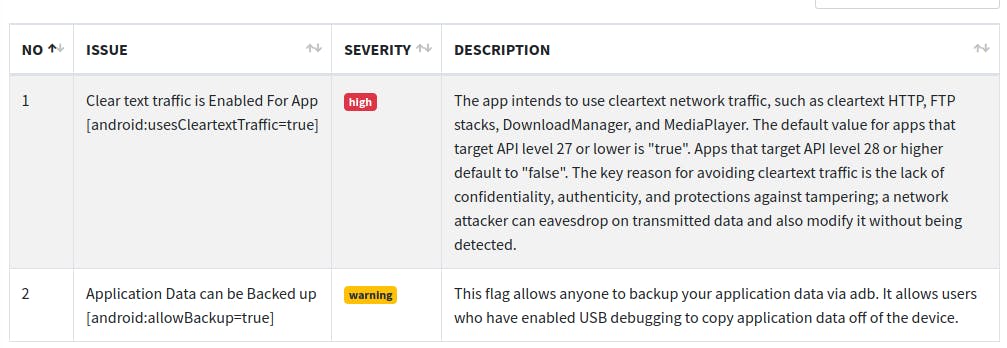
- Manifest Analysis
The next analysis fields, "Browsable Activites" and "Network Security", are emtpy, but the next point "Manifest Analysis" contains some interesting information.
For one thing, it claims that the app is communicating in cleartext. This is actually not fully true: Cleartext communication is permitted, but the default communication is ssl-encrypted by the C-library libssl.so (also included in the standard pil21 distribution).
Also, application data can be backed up which means that the data can be copied unencrypted from the device when connected to a computer. Again, it depends on the stored data if this is a problem or not.
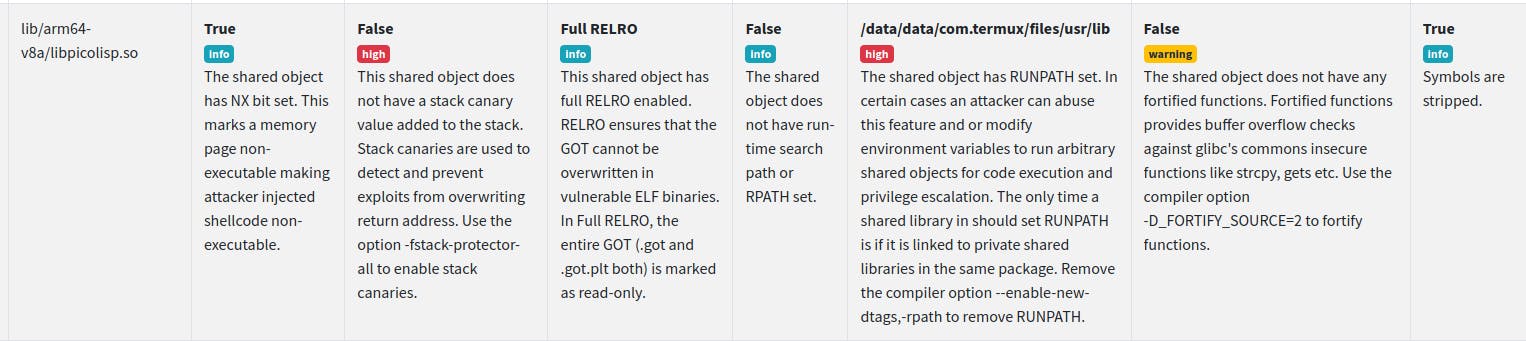
As last step, let's take a look at the shared library binaries. Here the security checker is complaining about runpath variables and missing stack canaries. I'm not 100% sure about the details, but potentially, these kind of settings can be abused by an attacker to gain system control. However, we should keep in mind that PilBox is already a powerful tool by itself, as it allows almost anything you can do within the scope of your app sandbox.
Conclusion
The PilBox is a powerful tool and allows you to do a lot of things on your smartphone which normally requires a full Android studio development environment. Obviously, this also means that the developer needs to know what they are doing. For example, for certain applications it might be needed to add additional safety features if the default ones from the PilBox app are not sufficient.
In the next post, we will see how to load and modify basic applications in to the PilBox.